Blog Archives
How to configure AppLocker Group Policy to prevent software from running
بسم الله الرحمن الرحيم
Firstly: What is AppLocker?
AppLocker is a set of Group Policy settings that evolved from Software Restriction Policies, to restrict which applications can run on a corporate network, including the ability to restrict based on the application’s version number or publisher.
- Click Start – All programs – Administrative Tools – Group Policy Management.
- Create or Edit Group Policy Objects.
- Expand Computer Configuration – Policies – Windows Settings – Security Settings – Application Control Policies – AppLocker .
- In right pane click on Configure rule enforcement
Note:
-
Executable rules: .exe, .com
-
Windows Installer rules: .msi, .msp
-
Scripts rules: .ps1, .bat, .cmd, .vbs, .js
- Under Executable rules check configured box and select Enforce rules then click ok

- In left pane under AppLocker right click on Executable Rules then select Create New Rule
- Select Deny and select what user or group will prevent.
Note:
Publisher rules: This condition identifies an application based on its digital signature and extended attributes. The digital signature contains information about the company that created the application (the publisher). The extended attributes, which are obtained from the binary resource, contain the name of the product that the application is part of and the version number of the application.
Path rules: This condition identifies an application by its location in the file system of the computer or on the network.
File hash: This condition identifies an application which is not digitally signed can be restricted by a file hash rule instead of a publisher rule.
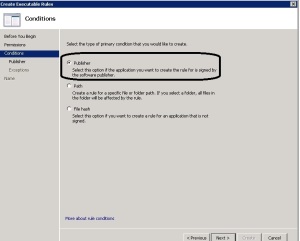
- Select Publisher and click Next
- Click browse then select executable file example.exe
- Choose any options from prevent with any publisher, publisher, product name, file name and file version then click Next.
- Read it and click Next
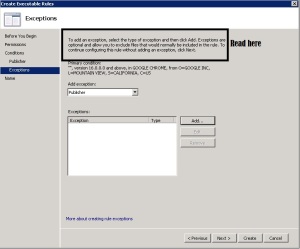
- Click Create

- You will now be prompted to create some default rules that ensure that you don’t accidently stop Windows from working. Click “Yes” to this if you don’t already have these rules created.

Note:
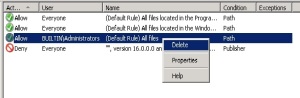
If you want to apply this role on computer administrator then right-click on the BUILTIN\Administrators rule and click Delete
Now we will active the Application Identity service to enable AppLocker on the computers
- In the same Group Policy Object you were just editing Computer Configuration – Policies – Windows Settings – Security Settings – System Services
- Right click Application Identity service then properties
- Check Define this policy setting box and Automatic then OK.

Now when users try run program he will get this
Reference:
http://www.windows7library.com/blog/security/applocker-part-2-understanding-applocker-rules/